How is classified information typically shared and can officials declassify secrets whenever they want? A national security expert explains
Published in News & Features
U.S. District Judge James Boasberg on March 27, 2025, ordered top Trump administration officials to preserve records of their messages sent on the messaging app Signal from March 11 to March 15 following a transparency watchdog group’s lawsuit alleging that the officials have violated the Federal Records Act.
This marked the latest development since The Atlantic on March 24 published a Signal chat among Defense Secretary Pete Hegseth, Secretary of State Marco Rubio and other national security officials discussing specific plans to attack Houthi militants in Yemen. Jeffrey Goldberg, the editor in chief at The Atlantic, was mistakenly included in the chat and wrote about what he saw.
Trump administration officials have shared contrasting accounts about whether they were discussing sensitive war information on Signal – but maintain that they did not share classified information.
Senator Roger Wicker, the Republican chair of the Senate Arms Services committee, and Senator Jack Reed, the top Democrat chairing the committee, on March 27 requested an investigation into how the Trump officials used Signal to discuss military strikes.
Amy Lieberman, a politics and society editor, spoke with national security scholar Dakota Rudesill to better understand what constitutes classified information and how the government typically handles its most closely kept secrets.
How are government officials supposed to communicate about classified information?
The first way someone with the proper clearance can communicate about classified information is in person. They can talk about secret things in what is called a sensitive compartmented information facility, or SCIF. This means a secure place, often with a big, heavy door and a lock on it, where security officials have swept the area for bugs and no one can easily eavesdrop. People who are in SCIFs usually have to leave their cell phones outside of the room, and then they can talk freely about secret information. A SCIF can be a particular room, or a floor of a building, or even an entire building.
Second, there is print communication: written documents with classification markings, which have to be handled in really particular ways, like in a safe location, and can be transported between SCIFs in secure containers.
Third, intelligence agencies, the White House and the Department of Defense also all have secure electronic systems. These include visual teleconferences, which are similar to a Zoom call and are secure for discussing highly classified information, as well as secure email systems and secure phones.
Many people with clearances have what is called “high side” email, which is shorthand lingo for classified email and messaging. Many people with security clearance would have two work hard drives and two computers. One of them is “low side,” where there is access to unclassified official email, documents and the internet.
All of these methods of secure communication can be clunky and take more time than people in our smartphone age are used to. That is the cost of protecting the nation’s secrets. My sense is the Trump administration officials wanted to move fast and turned to Signal, a commercial app that promises encryption. Signal is generally considered secure but is not perfect. There is abundant public evidence that Signal is not totally secure and indeed has been penetrated by Russian intelligence.
Can something be declassified after the information has been shared?
Yes. The president can classify and declassify at will via oral or written instruction.
The president’s constitutional powers include removing classification controls after information has been released or leaked. Trump could at any point declassify the information shared on Signal. Several of the Cabinet-level officials on that Signal chat also have expansive delegated powers over classification.
Even so, Trump’s national security Cabinet would have presumably still violated the law. For example, by putting national defense information inappropriately on an insecure app and not checking to verify the clearances of everyone on the chat and thereby allowing a reporter to be present, one could reasonably conclude that the team was showing “gross negligence,” running afoul of the Espionage Act.
The Espionage Act, enacted in 1917, criminalizes unauthorized retention and dissemination of sensitive information that could undermine the national security of the U.S. or help a foreign country.
Was the information shared on Signal likely classified?
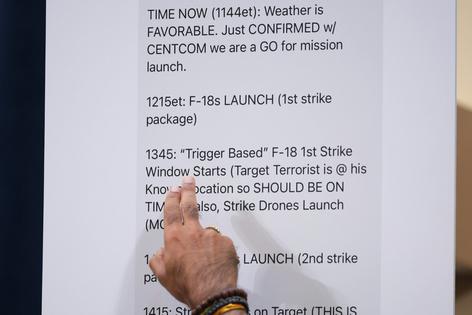
Looking at the Signal message transcript that The Atlantic shared, it seems like at least four things were all but surely classified.
The most obvious was the details that Secretary of Defense Hegseth provided on the strike plans. These include the precise times that planes were taking off, what kind and when the bombs would fall. Recent reports have quoted defense officials confirming that this information at the time was classified.
Second, the chat revealed that the president gave a green light for secret strikes at a Situation Room meeting.
Third, there is the mere fact of these top officials deciding whether and when to execute attacks authorized by the president.
And fourth, according to media reports, the chat included the name of an intelligence officer whose position may have been secret.
The Trump administration says that there was no classified information in the chat. But several analysts have noted that defies belief. The exception would be a prior decision to declassify, but we have no evidence of that.
What other issues does this bring to mind?
First, we don’t know whether the Trump officials carefully thought about it before they set up this chat on Signal, which the Pentagon has warned government officials against using because of hacking concerns.
Second, even if the officials did make a focused decision to use Signal, what is the wisdom of that? I find it really, really hard to imagine that was a prudent decision when we think about how insecure this app is. There is also the fact that Steve Witkoff, Trump’s envoy to Ukraine and the Middle East, was party to the chat while he was in Russia. We do not know for sure if he had a device running Signal on him personally while he was in Russia, but in any event he would have been under intense Russian surveillance.
A broader issue is how the Trump administration is enforcing the law is a giant question mark. Usually, the law both authorizes the U.S. government to do things, and also says it cannot do things. Law enables and limits everyone, including the president. However, Trump wrongly claims that he is the final authority on the law, and so far the Justice Department only seems to be enforcing the law against people outside of the administration.
So does the law limit the Trump administration in any practical sense? Right now it is not clear – and there is abundant reason to be concerned about that from a rule of law standpoint.
This article is republished from The Conversation, a nonprofit, independent news organization bringing you facts and trustworthy analysis to help you make sense of our complex world. It was written by: Dakota Rudesill, The Ohio State University
Read more:
Signal is not the place for top secret communications, but it might be the right choice for you – a cybersecurity expert on what to look for in a secure messaging app
From Greenland to Fort Bragg, America is caught in a name game where place names become political tools
US swing toward autocracy doesn’t have to be permanent – but swinging back to democracy requires vigilance, stamina and elections
Dakota Rudesill does not work for, consult, own shares in or receive funding from any company or organization that would benefit from this article, and has disclosed no relevant affiliations beyond their academic appointment.












Comments